X (formerly Twitter) is experiencing its third major outage of the day, with users reporting widespread login and loading issues. The hacking group Dark Storm Team has reportedly claimed responsibility for a DDoS attack on the platform, according to a public Telegram post.
Newsweek has reached out to the X via email for comment on the matter.
What to know:
- More than 40,000 reports flooded Downdetector during the second outage.
- The current outage peaked at 29,143 reports and is now slightly declining.
- Dark Storm Team claims to have targeted X with a cyberattack.
- Users are unable to access the site, with many receiving error messages.
- This marks the third significant disruption to X’s service today.
Stay with Newsweek for updates on the latest X outage as the situation develops.
Signs of a DDoS attack to watch out for
The most obvious sign of a DDoS attack is when a website or service suddenly becomes slow or unavailable, according to Cloudflare. However, since other factors like a legitimate surge in traffic can cause similar issues, further investigation is often necessary. Traffic analytics tools can help identify signs of a DDoS attack.
Some telltale signs include suspicious traffic volumes coming from a single IP address or IP range, or a surge in traffic from users with similar behavioral profiles, such as the same device type or geolocation. An unexplained increase in requests to a particular page or endpoint is another red flag.
Additionally, odd traffic patterns, such as spikes at unusual times or frequent spikes at regular intervals (e.g., every 10 minutes), could indicate a DDoS attack in progress. While these are general indicators, more specific signs can vary depending on the attack’s nature.
Crash course on DDoS: How botnets fuel DDoS attacks
DDoS attacks are carried out using networks of internet-connected machines, often referred to as botnets. These botnets consist of computers and other devices, like IoT devices, that have been infected with malware, allowing an attacker to control them remotely. The individual infected devices are known as bots, and when grouped together, they form a botnet.
Once a botnet is established, the attacker can direct it to carry out an attack by sending remote instructions to each bot. In a typical DDoS attack, the bots send numerous requests to the target’s IP address, overwhelming its server or network. This can result in a denial of service, blocking legitimate traffic from accessing the service.
Since each bot is a legitimate internet device, distinguishing between attack traffic and regular user traffic can be extremely difficult, making DDoS attacks challenging to defend against.
Crash course on DDoS: What is it?
The hacking group Dark Storm Team has reportedly claimed responsibility for a DDoS attack on X. But what is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network, as defined by Cloudflare, a network that helps websites and services run faster and more securely. This is done by overwhelming the target or its surrounding infrastructure with a flood of internet traffic, rendering it inaccessible to legitimate users.
DDoS attacks are effective because they use multiple compromised devices as sources of attack traffic. These devices can include computers, IoT devices, and other networked resources that have been exploited for the attack.
In simpler terms, a DDoS attack is like a traffic jam on a highway that prevents regular traffic from reaching its destination. The scale and severity of the attack depend on how many compromised devices are involved, making it a significant concern for online services and businesses.
X/Twitter is down for a third time today
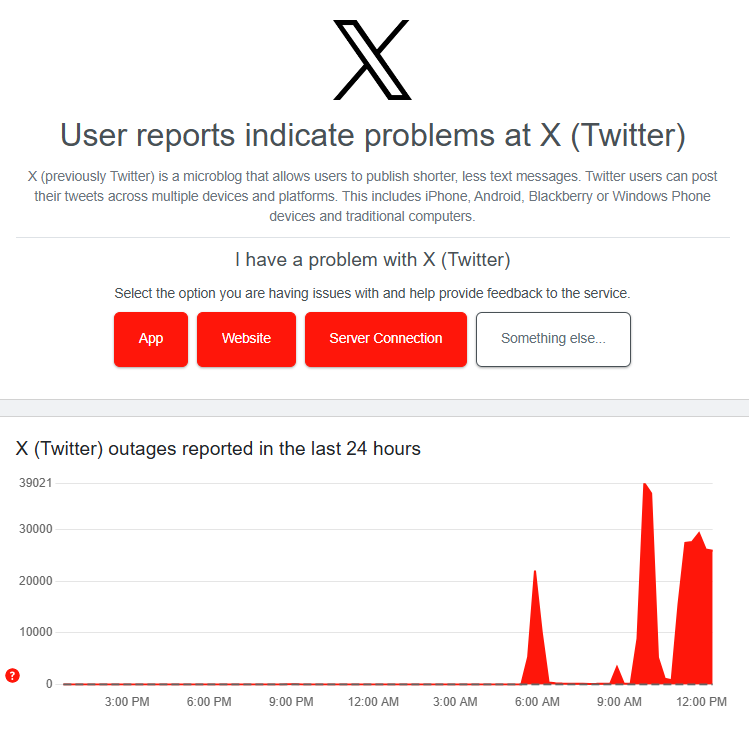
Screenshot/Downdetector
There have been three outages involving X, formerly Twitter, on Monday.
Thousands of users have experienced issues logging onto the platform, with users mostly complaining of issues with the app at 57%, according to outage tracker Downdetector.
This article was originally published by a www.newsweek.com . Read the Original article here. .

